In addition to several bug fixes, the iOS 18.0.1 and iPadOS 18.0.1 updates released on Thursday include a few security […]
Tag: security
Firefox 131 brings tab previews, text fragment links, and security fixes
Yesterday, Mozilla released Firefox 131 for Windows, macOS, Linux, and Android, which not only fixes a number of security vulnerabilities […]
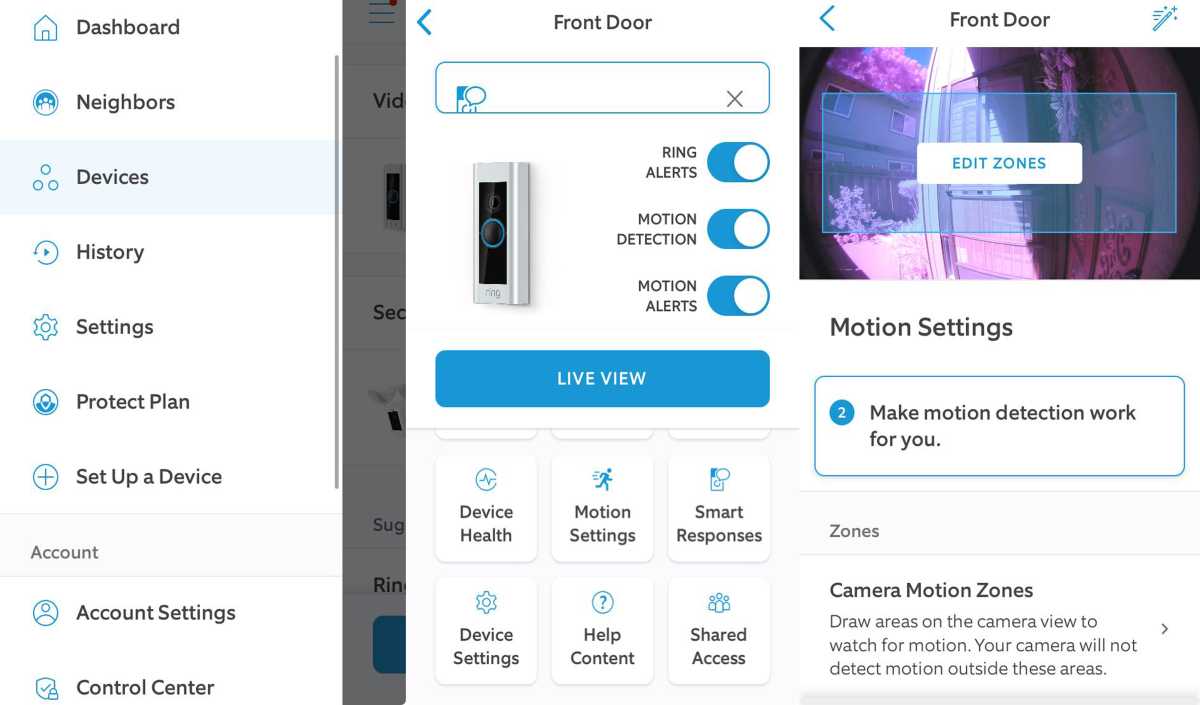
7 Ring camera video settings that will bolster your home security
When it comes to home security, video quality is more than just a luxury—it’s a necessity. Clear, detailed footage can […]
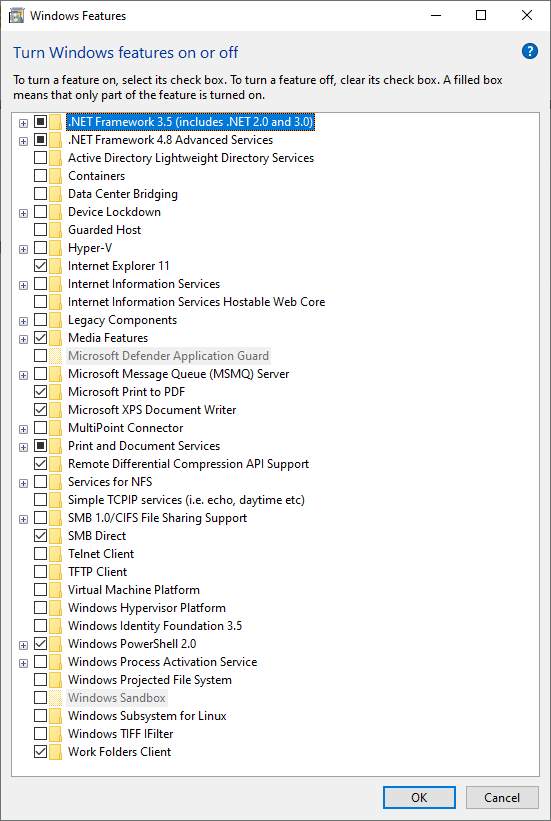
This one security feature makes Windows 11 Pro worth every penny
I swear to you that I’m not pirating software, movies, or TV shows. Nor am I downloading anything “adult” while […]
Is Your Gear Safe? Some Security Dos and Don’ts: Tops and Flops
It’s easy to overlook security in your working space, be it a bedroom studio or something a little bigger. We […]
Hackers know your social security number. Here’s how to stay safe
For anyone trying to keep their personal information secure, recent headlines have been a grim kick in the pants. The […]
Upgrade to Windows 11 Pro for $20 and unlock advanced features for work, play, and security
TL;DR: Upgrade your PC to Windows 11 Pro for $19.97 through September 29 and enjoy enhanced security, better multitasking, and […]
Edera is building a better Kubernetes and AI security solution from the ground up
Edera, a startup looking to simplify and improve how Kubernetes containers and AI workloads are secured by offering a new […]
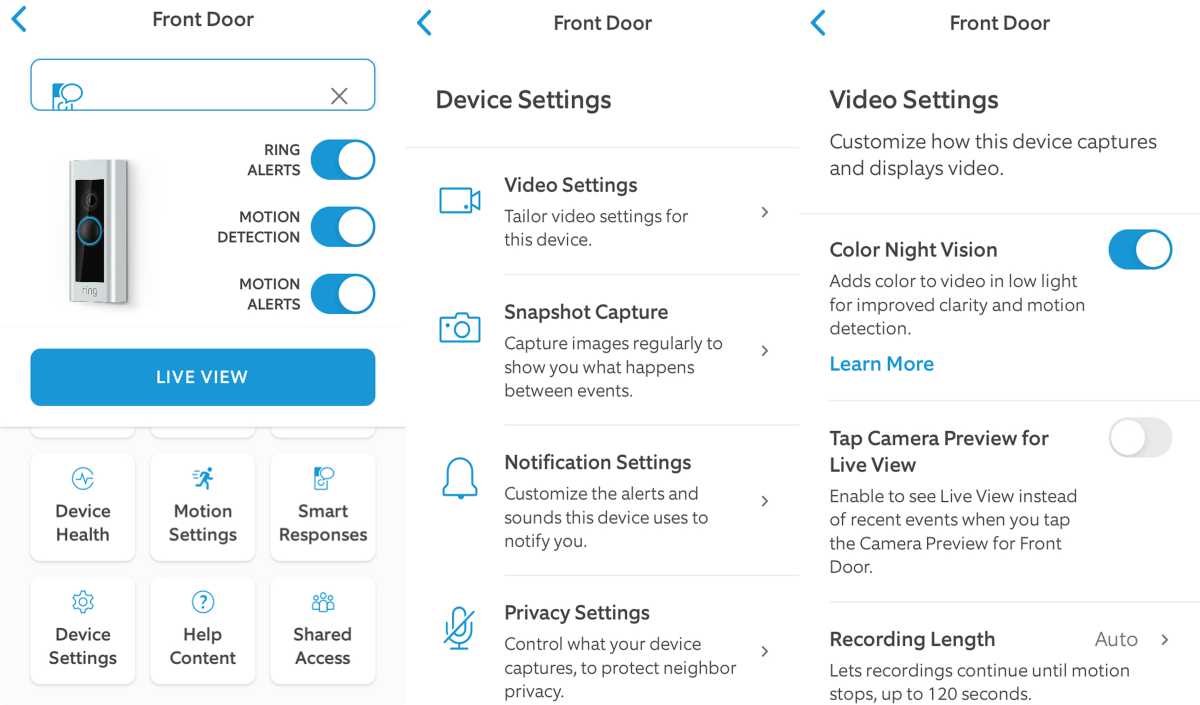
These 9 Ring security cam settings will make your home safer
The effectiveness of Ring security cameras and video doorbells is determined by more than their image quality; it’s also about […]
Apple Fixes Vision Pro Security Flaw That Could Expose What You Typed
As reported by WIRED today, a group of six computer scientists this year discovered a security vulnerability with the Apple […]